Joint solution enables seamless vulnerability detection, prioritization and agile virtual patching for web applications, web services and APIs.
Gartner forecasts fast growth in the security testing market due to continued data breaches and growing demands for application security testing as part of DevOps.
To enable simple, cost-effective, agile and reliable application security testing and risk-based remediation, High-Tech Bridge has partnered with Fortinet to deliver a solution tailored for DevSecOps and CI/CD facilitation. The partnership enables organizations to remediate web application vulnerabilities within minutes and at no additional costs, including security flaws affecting REST/SOAP APIs and Single Page Applications.
High-Tech Bridge’s ImmuniWeb® AI Platform leverages Machine Learning and AI for intelligent automation and acceleration of application security testing. Complemented by scalable and cost-effective manual testing, it detects the most sophisticated vulnerabilities and comes with a zero false-positives SLA. ImmuniWeb’s groundbreaking virtual application technology enables its customers to test both internal and external web applications and leverage award-winning IAST technology.
Fortinet’s FortiWeb Web Application Firewall provides advanced features that defend web applications from known and zero-day threats. Using an advanced multi-layered and correlated approach, FortiWeb provides complete security for your external and internal web-based applications from the OWASP Top 10 and many other threats. At the heart of FortiWeb are its dual-layer AI-based detection engines that intelligently detect threats with nearly no false positive detections.
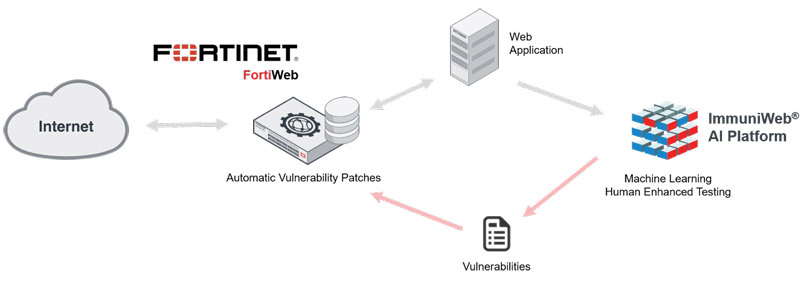
Once ImmuniWeb AI audit results are imported to FortiWeb, then FortiWeb virtual patching automatically creates new WAF rulesets to protect against newly discovered vulnerabilities and weaknesses.
The joint solution eliminates the perilous gap when a newly detected security flaws remain unaddressed and exploitable. It thereby enables web developers to properly test and deploy a security patch without exposing their enterprise to the risk of data breach.
“Modern organizations face a continuously growing landscape of security tasks of an increasing sophistication. The challenge is exacerbated by global cybersecurity skills shortage and the large number of different security products required to enable continuous security monitoring, risk-based remediation and cyber resilience,” said Ilia Kolochenko, CEO and Founder of High-Tech Bridge. “At High-Tech Bridge, we are excited to join our efforts with global cybersecurity leader Fortinet to deliver a turnkey application security solution. Our research in AI and Machine Learning technology offers unprecedented accuracy, speed and reliability to our clientele. The joint solution is, however, a mere beginning of our partnership journey aimed to bring sustainable and long-term value to the customers and to the application security market as whole. Please stay tuned.”
“The Fortinet Security Fabric’s open architecture, APIs (Application Programming Interfaces) and ease of integration with complementary technologies from our alliance partners enable highly effective security solutions to address customer needs,” said Neil Prasad, Senior Director of Product Marketing and Global Technology Alliances at Fortinet. “We welcome High-Tech Bridge in our Fortinet technology alliance partner program and ecosystem, and look forward to our collaboration to provide a more secure future for all our customers.”
Additional Resources
- Read more about High-Tech Bridge’s ImmuniWeb® AI Platform.
- Read more about the Fortinet Security Fabric, the FortiWeb Web Application Firewalland the joint solution.










