Reports about an Amazon data breach are spreading fast and furiously, although the online retailer denies that what happened was actually a breach. At least one expert is siding with Amazon on this, but to the average consumer, it may seem like splitting hairs.
Black Friday is only days away, so many shoppers are making decisions about where to spend their hard-earned cash. This could be one reason the company is being so secretive about this alleged data breach.
Amazon data breach reports stem from emails
Amazon emailed a number of shoppers on Tuesday to report that its website had “inadvertently disclosed” their name and email address “due to a technical error.” The online retailer also said it has fixed the issue, so users don’t have to do anything else.
Social media users were quick to start posting about the email and expressing concern about this potential Amazon data breach. Some even questioned whether the email they had received was genuine, pointing out details about the email which made it look like a phishing message. However, the online retailer has confirmed to multiple media outlets and news blogs that the email was real. However, beyond those generic statements, Amazon is remaining tight-lipped.

News outlets and tech blogs have been trying to get more details from the company about the data leak, but spokespeople are refusing to say anything more about it. They won’t say how many customers were infected, what caused
the leak, or how long it took them to realize there was a problem.
Amazon data breach may not have been a breach at all
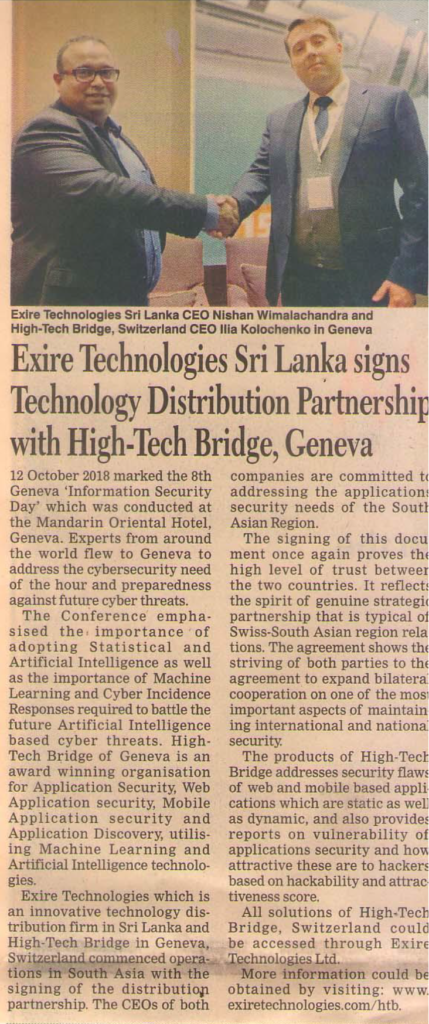
Amazon’s U.K. office denies that there was a breach, in the technical sense of the word, and the founder of a web security company agrees, although he admits that more details are needed. High-Tech Bridge CEO and founder Ilia Kolochenko advised against drawing “premature conclusions” about the alleged Amazon data breach until more technical information is available, but he also urged the company to stop being so tight-lipped about the issue.
“Based on the information currently available, it is technically incorrect to call this incident a ‘data breach,’ he said in a statement. “This rather looks like an inadvertent programming error that made some details of Amazon’s profiles publicly available to random people… Amazon’s reaction seems to be quite prompt, however an official statement would certainly be helpful to prevent any speculation and unnecessary exaggeration of the incident and its scope.”
For those who like splitting hairs, the incident may be considered more of a data leak than a data breach, in that Amazon appears to have accidentally exposed users names and email addresses. A breach, on the other hand, involves someone hacking into a database or network and gaining unauthorized access.
Nonetheless, consumers will likely see this incident as an Amazon data breach because at the end of the day, the average shopper cares only that their information was exposed. It matters little whether their data was exposed thanks to a hacker or an accidental leak.
Shoppers prepare for Black Friday
The reported Amazon data breach comes just two days before Black Friday, one of the busiest shopping days of the year. This could be one reason the company is trying to keep a tight lid on information about the incident. Because of the data leak, shoppers may hesitate to spend money on Amazon on Black Friday or even later in the holiday shopping season.
Ref: Author: Michelle JonesMichelle Jones was a television news producer for eight years. She produced the morning news programs for the NBC affiliates in Evansville, Indiana and Huntsville, Alabama and spent a short time at the CBS affiliate in Huntsville. She has experience as a writer and public relations expert for a wide variety of businesses. Michelle has been with ValueWalk since 2012 and is now our editor-in-chief. Email her at Mjones@valuewalk.com.