How Secure Are You?
HARNESS THE HACKER
Quantify enterprise risks
Simulate breach methods across the entire kill chain based on attacker profile and data assets to be protected. Quantify the real impact of a cyber attack on your systems, and see risk trends over time. Identify remediation options to stay one step ahead of the bad guys.
Validate security controls
Continuously validate how well your security controls are working using our Hacker’s PlaybookTM of breach methods. Quickly address configuration, segmentation or implementation errors throughout the entire lifecycle of a security product.
Weaponize threat intelligence
Transform threat intelligence Indicators of Compromise (IoCs) into breach methods to see how specific attacks will play out. See if new attacks will be successful, or will be blocked. Establish a security baseline, and ensure ongoing configuration and policy updates improve security posture, with continuous breach and attack simulation.
This quick animated video, just one minute in length, will show how the SafeBreach can help security leaders identify and quantify the impact of a breach before it happens.
A Platform Approach
To Offensive Security
Our unique software platform simulates adversary breach methods across the entire kill chain, without impacting users or your infrastructure. SafeBreach holds multiple patents for the Breach and Attack Simulation technology (U.S. Patent No.9892260, U.S. Patent No. 9710653, U.S. Patent No. 9473522)
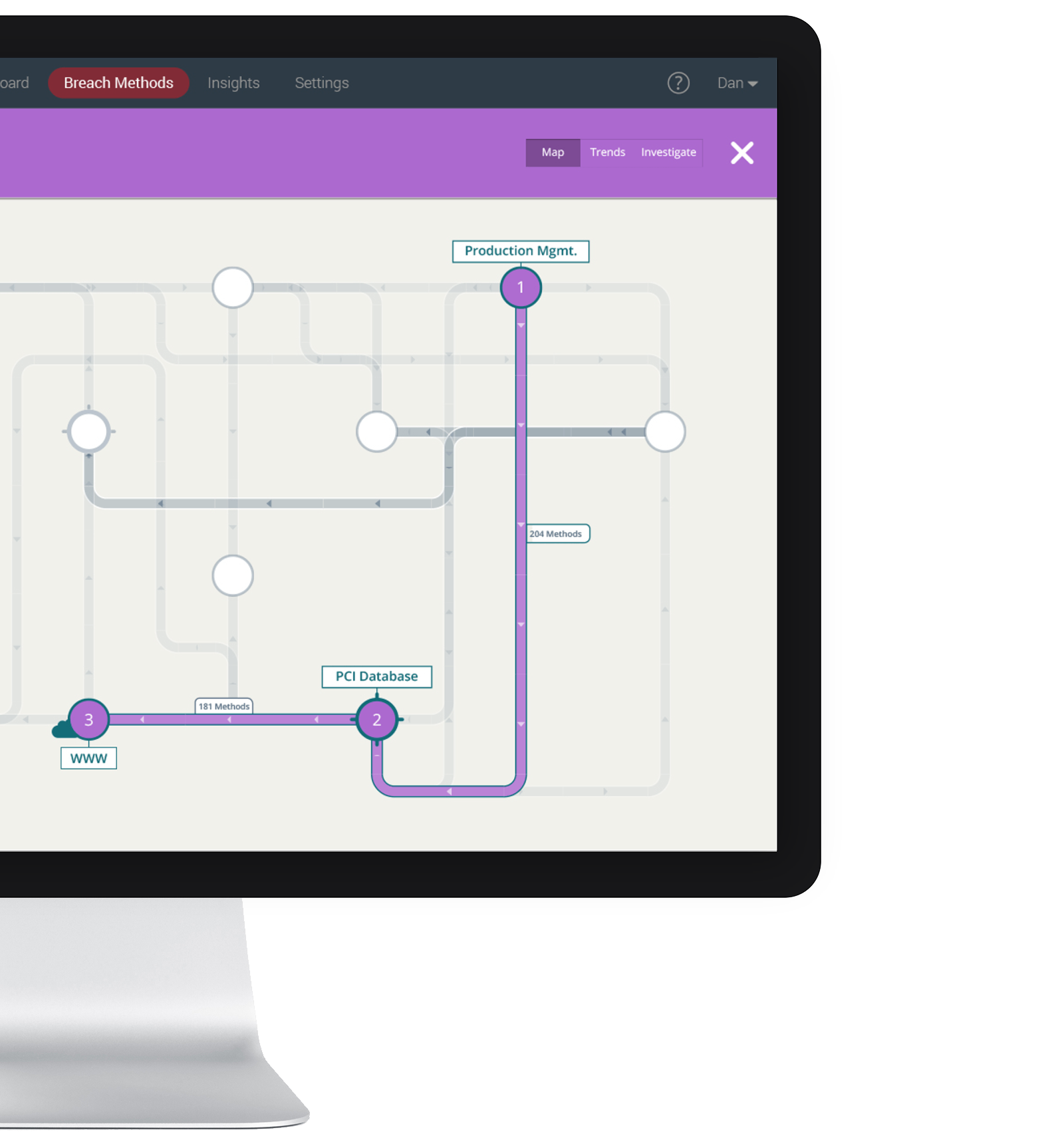
Deploy simulators to “play the hacker”
SafeBreach lightweight simulators play the role of the hacker. Deploy them in critical segments of your network, in the cloud and on endpoints to simulate the entire kill chain – infiltration, lateral movement, and exfiltration. Cloud, network and endpoint simulators are available.
Orchestrate and execute breach scenarios
The Safebreach management server incorporates the Hacker’s Playbook™ of breach methods and manages the distributed network of simulators. Our patent-pending technology simulates breach scenarios to validate the effectiveness of your security controls, without impacting users or infrastructure. Breach methods are constantly updated by SafeBreach Labs, our team of offensive security researchers.
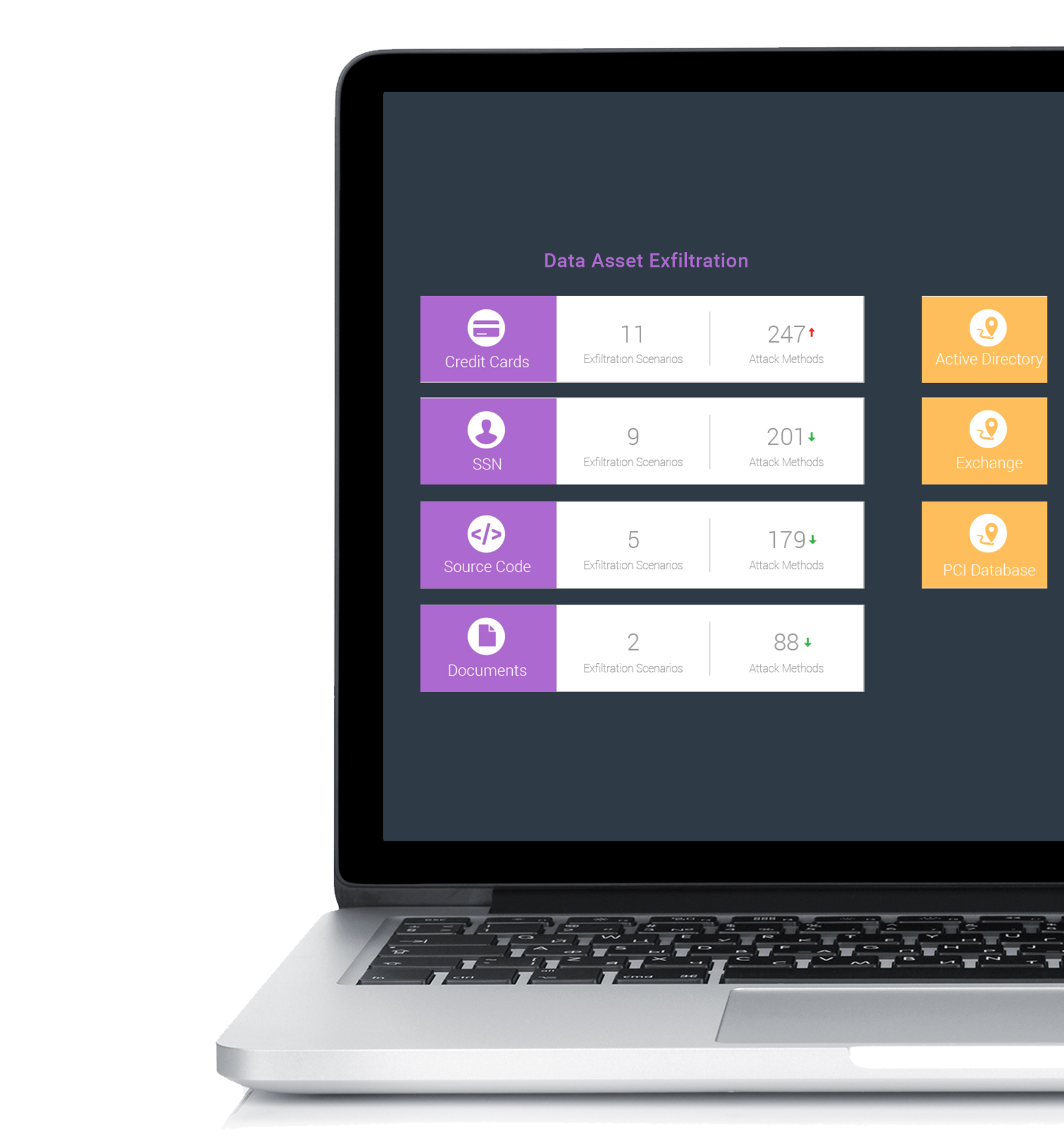
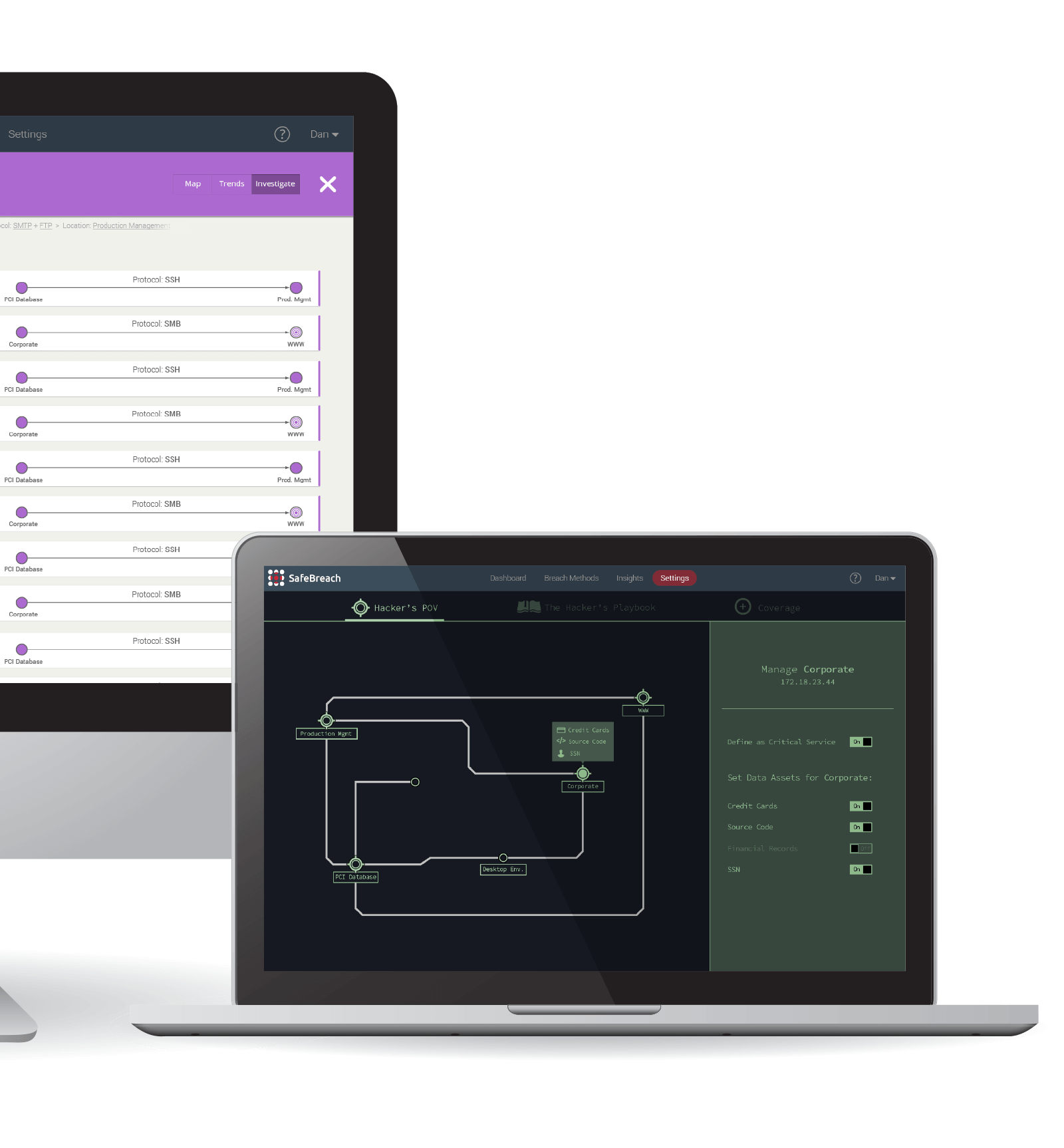
Quickly take corrective action
Our platform correlates and analyzes all breach methods, and presents information useful for both security analysts and security executives. See risk trends over time, drill into specific findings, and remediate quickly based on SafeBreach recommendations. Integrate with SIEMs, ticketing systems, threat intelligence feeds and automation/orchestration vendors.
Continuously Validate
Continuously simulate breach methods to address changing risks. Re-run breach methods when changes are made to security products. Track your security posture via risk trending and historical reports. Use our business insights to engage and educate the board on your true security risks.

